You are looking for a way to acquire an access token from Azure Active Directory without user interaction. We highly recommended to always use an interactive user sign-in experience as this is the most secured method. Especially when your organization has conditional access policies which require Multi-Factor Authentication. If at all possible, please use the methods for interactive sign-in.
Here are some general guidance on how to non-interactively acquire a access token.
Client Credentials grant flow (Recommended)
https://docs.microsoft.com/en-us/azure/active-directory/develop/v1-oauth2-client-creds-grant-flow
Note: There are some services that does not support the client access token issued when using Client Credentials.
Resource Owner Password Credential grant flow (Not recommended)
https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc
Note Only use this if Client Credentials is not supported for the resource and no other flows are an option. Also only use if the application is behind a protected and secured environment
On-behalf-of flow
https://docs.microsoft.com/en-us/azure/active-directory/develop/v1-oauth2-on-behalf-of-flow
When trying to use ADAL/MSAL
It will attempt to pull the federation services metadata to get the active endpoint (i.e. if your using AD FS, this is the usernamemixed endpoint) and will send the user name and password to the active endpoint. If you get errors, you will need to troubleshoot the federation service. Active endpoint must be publicly available and token issuance policy rules must allow the call to the usernamemixed endpoint. (Hint: Generally when you have legacy authentication configured to be blocked, this will also impact the call to the usernamemixed endpoint.)
Note: If you can’t get this resolved from the federation service, then consider using a cloud only user account or do not use ADAL/MSAL at all.
I would suggest making your application registration a Native App or aka Public Client. This is because ADAL/MSAL does not have any methods for Resource Owner Password Credential flow if the application registration is a Web App. Generally with web applications, it is expected that you will be using one of the other flows I.e. Authorization Code or On-behalf-of.
There are two ways to ensure the authentication is using the application as the Native Client (Public Client) context…
Method One: Use a Public Client redirect URI…
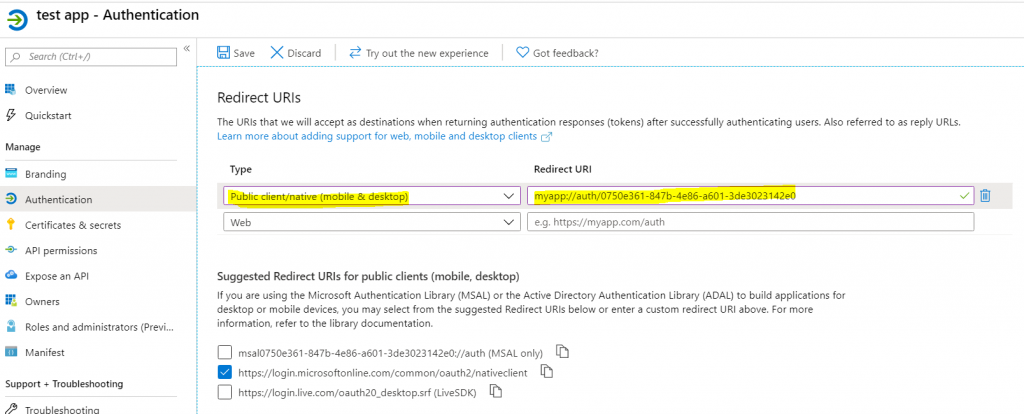
Method Two: Enable Default client type as public client…
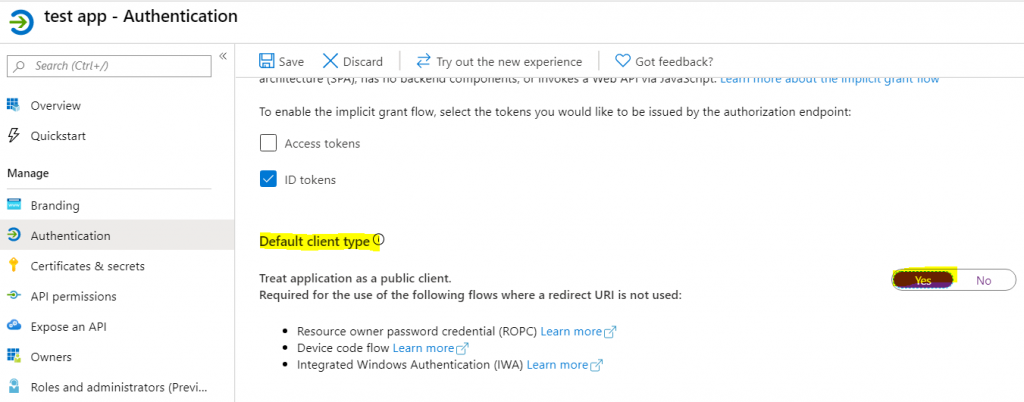
Example…
For example when using ADAL.NET, the code will look something like this…
//... UserPasswordCredential user; user = new UserPasswordCredential(userName, password); result = authContext.AcquireTokenAsync(resourceId, clientId, user).Result; //...
When you are calling the token endpoint directly…
So you are attempting to perform Resource Owner Password Credential flow directly based on the following guidance…
https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc
You might get the following similar error message…
AADSTS50126: Error validating credentials due to invalid username or password.
Ensure Direct Authentication is enabled…
To do this…
- Make sure AzureAdPreview PowerShell module is installed
https://www.powershellgallery.com/packages/AzureADPreview/2.0.2.129 - Run the following PowerShell Command to create a new Azure AD Policy for Direct Authentication…
$policyid = New-AzureADPolicy -Definition @("{"HomeRealmDiscoveryPolicy":{"AllowCloudPasswordValidation":true}}") -DisplayName EnableDirectAuthPolicy -Type HomeRealmDiscoveryPolicy - Then apply the policy to the ServicePrincipal object (Enterprise App)
Add-AzureADServicePrincipalPolicy -Id <ObjectID of the Service Principal> -RefObjectId $policyid
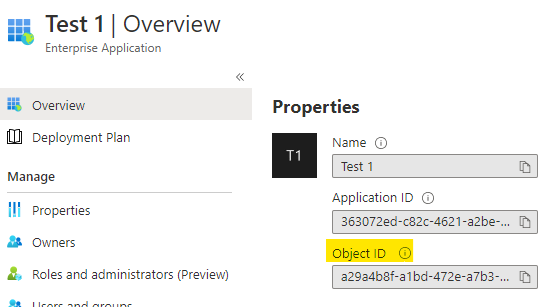
For more information see…
And ensure Password sync is enabled…
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-password-hash-synchronization
If you’re not able to enable Direct Authentication or enable Password sync, then you will not be able to use a Federated user account. In that case, you will need to use a non-federated user account. This can be done by creating a new user account in the Azure AD portal using any of the other non-federated domains.
Temporary passwords and password resets are not synchronized to Azure AD.
Keep these in mind…
Keep in mind you might have conditional access policies that may block you from getting a token non-interactively. If that’s the case, discuss with your security team. If you get approval to allow this non-interactive token acquisition, then add the user as an exception to the conditional access policy.