Below are the basic steps for using PostMan to test a B2C Resource Owner Password Credentials ( ROPC ) policy. You will need a set of user credentials along with a Application ID of a B2C Native application that will be used to retrieve the token.
Obtain the token endpoint from the B2C ROPC Policy
1. In the portal, locate the B2C blades by searching for B2C, then locate the “Resource Owners Policies” item and click it.
2. In the list of policies to the right, Click the name of the policy.
3. Locate the ROPC Policy URL and click.
4. In the JSON that is displayed in the Brower, make a note of the “token_endpoint” property.
{
“issuer”: https://login.microsoftonline.com/f06c2fe8-709f-4030-85dc-38a4bfd9e82d/v2.0/,
“authorization_endpoint”: https://login.microsoftonline.com/casalaola.onmicrosoft.com/oauth2/v2.0/authorize?p=b2c_1_maxv_b2c_ropc_policy,
“token_endpoint”: https://login.microsoftonline.com/casalaola.onmicrosoft.com/oauth2/v2.0/token?p=b2c_1_maxv_b2c_ropc_policy,
“jwks_uri”: https://login.microsoftonline.com/casalaola.onmicrosoft.com/discovery/v2.0/keys?p=b2c_1_maxv_b2c_ropc_policy,
“response_modes_supported”: [
“query”,
“fragment”,
“form_post”
],
….<JSON content removed for brevity>
}
In this example the token URL would be:
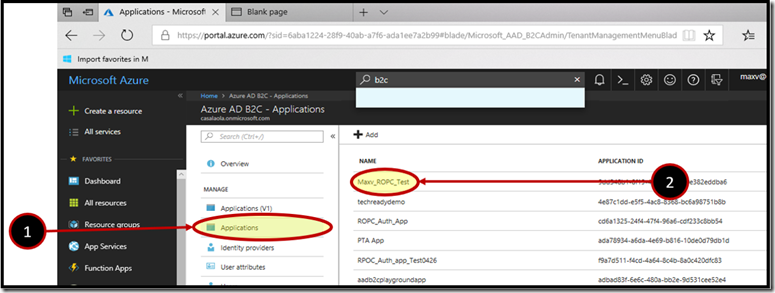
Obtain the Application ID of the B2C Native application that will be used to request the token.
-
- In the B2C main blade click the Applications menu item.
- Then click the target application from the list of applications to the right.
3. On the Properties blade of the application. Locate the Application ID and click the clipboard icon ![]() to its right.
to its right.
You will need this GUID when you build the PostMan request
In this example the application id would be:
9dd348b1-8f19-49c9-82ee-10e382eddba6
Build the token request using PostMan
1. Start PostMan desktop application. If you need to install PostMan visit the following URL:
https://app.getpostman.com/app/download/win64
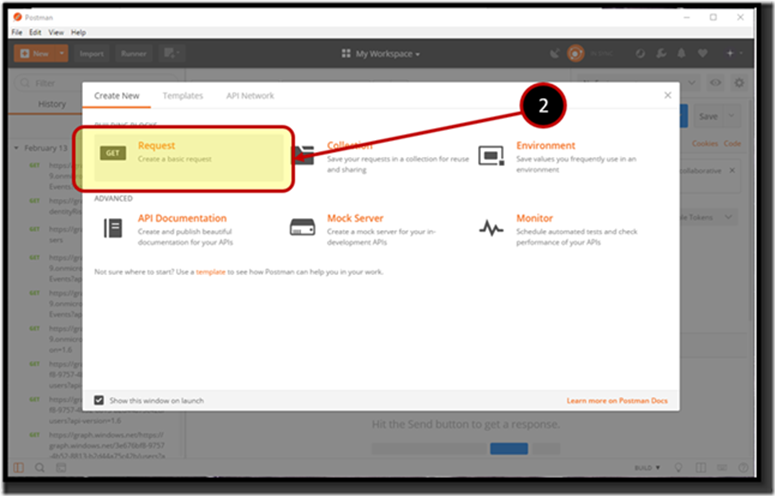
2. Click the New button or if you allow the Create New wizard to launch at start up, click Request region.
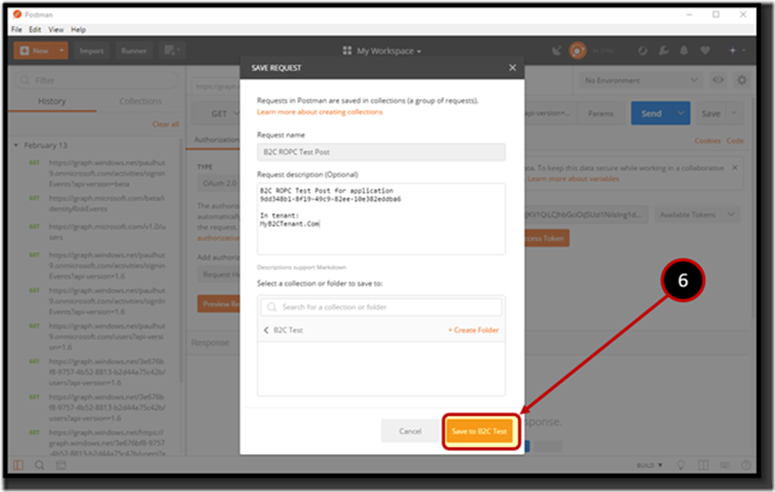
3. In the SAVE REQUEST box, give the request a name, in this example the name chosen is “B2C ROPC Test Post”. Add a description that makes sense to you.
4. If you have no collections, create “B2C API Testing” collection, you can name the collection whatever you like or add the request to an existing collection.
5. Click the “Create Folder” or select a collection from the folder list.
6. Click the “Save To….” Button.
7. Select “POST” from the operation type drop down.
8. Place the token URL for the application in the “Enter Request URL” edit control. In this example post, the URL would be:
https://login.microsoftonline.com/casalaola.onmicrosoft.com/oauth2/v2.0/token?p=b2c_1_maxv_b2c_ropc_policy
9. Click “Body” section of the request
10. Click the “x-www-form-urlencoded” radio button ![]() .
.
NOTE:
If you add the key value pairs before clicking the radio button, you will be required to renter the key values pairs once again. Be sure to click the x-www-form-urlencoded radio button first.
11. Add the key value pares from the following table:
| Key | Value |
| username | UPN Of User you want to request a JWTToken for |
| password | Corresponding Password for the username |
| grant_type | password |
| scope | openid <appId Guid> <other scoping parameters> |
| client_id | <application ID of the app you want to test> |
| response_type | token id_token |
The values for this example would be:
| Key | Value |
| username | zbfp@outlook.com |
| password | (HeartOfGold) |
| grant_type | password |
| scope | openid 9dd348b1-8f19-49c9-82ee-10e382eddba6 |
| client_id | 9dd348b1-8f19-49c9-82ee-10e382eddba6 |
| response_type | token id_token |
The “Headers” tab will be automatically populated.
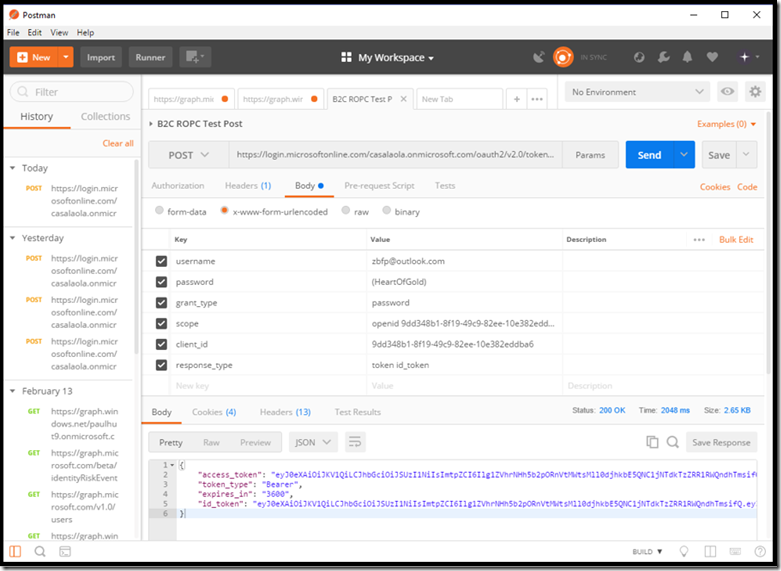
The post should look similar to the following:
13. The Status code will be 200 if the request is successful. If there is an error. The body of the request will contain the specific error.
14. The response will contain the token information if successful. You can use a site like http://jwt.ms to decode, both, the access_token and id_token properties. The following illustration is an example of a successful POST to a B2C ROPC Policy token end point:
![clip_image002[4] clip_image002[4]](/wp-content/uploads/2018/05/clip_image0024_thumb.png)
![clip_image004[4] clip_image004[4]](/wp-content/uploads/2018/05/clip_image0044_thumb.png)
![clip_image009[6] clip_image009[6]](/wp-content/uploads/2018/05/clip_image0096_thumb.png)
![clip_image016[6] clip_image016[6]](/wp-content/uploads/2018/05/clip_image0166_thumb-1.png)
![clip_image017[4] clip_image017[4]](/wp-content/uploads/2018/05/clip_image0174_thumb-1.png)