Let get started!
This article assumes you are using your own code to perform the authentication to Azure Active Directory.
IMPORTANT: So if your using Azure App Services or Azure Function Apps Authentication/Authorization feature, this article is not for you.
You are developing a Asp.Net OWIN or Asp.Net Core Authentication web application and integrating it with Azure Active Directory. You run into some issues during the sign-in process with no error message or any hint on what the problem might be. Some of the behaviors that you might see are…
- The dreaded infinite loop between your web app and Azure Active Directory.
- After signing into Azure Active Directory, you land back on to your Web Application like it never signed in.
- You land on your error page with no useful error message.
The purpose of this article is not to show you how to resolve the failed sign-in attempt. Rather, I want to show you how to troubleshoot and maybe expose the hidden error message. Once you have unraveled the hidden error message, hopefully that will lead you down a path to resolve the failed sign-in attempt.
This is where the OnAuthenticationFailed notification comes in handy…
In Asp.Net, you want to make sure your code looks something like this for the for the AuthenticationFailed event notification event notification (in startup.auth.cs)…
[gist id=”5773aac85537d35ca0f0d496d1e7b581″ file=”AspNet_OWIN_OnAuthenticationFailed.cs”]
In Asp.Net Core, you want to make sure your code looks something like this for the for the OnAuthenticationFailed event notification event notification (in startup.cs)…
[gist id=”813dd19091dfa8650895182cb45d5d1c” file=”AspNetCore_Auth_OnAuthenticationFailed.cs”]
You can of course tweak this so that you can either send the error message to your logs or send it to a custom error page.
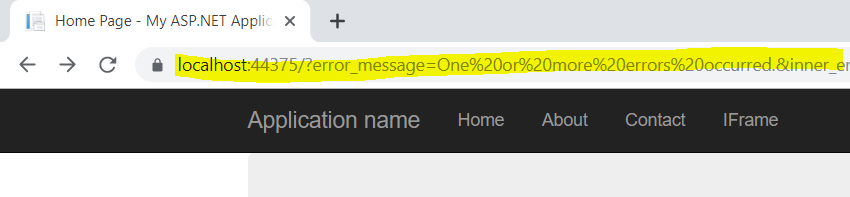
At minimum, we should see the error message in the address bar…
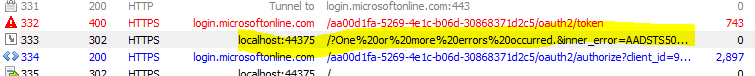
or in the case of the infinite loop, see it in the Fiddler capture…
For more information about using Fiddler, check out our Blog post here…
For a list of Azure Active Directory errors and and some tips on how to resolve, check out the following article…
https://docs.microsoft.com/en-us/azure/active-directory/develop/reference-aadsts-error-codes