You may get the following 403 error when using Microsoft Graph Security API to call various end points (https://graph.microsoft.com/v1.0/security/alert, https://graph.microsoft.com/beta/security/secoreScores, etc…)
“Auth token does not contain valid permissions or user does not have valid roles”
Root Cause
The above error can occur if the access token is missing the following requirement:
- The token does not have the required Microsoft Graph permission for the https://graph.microsoft.com/v1.0 (or beta)/security/xxx entity endpoint being used
- The authenticating user obtaining the access token is not in one of the required Azure AD admin roles (for delegated permission type token)
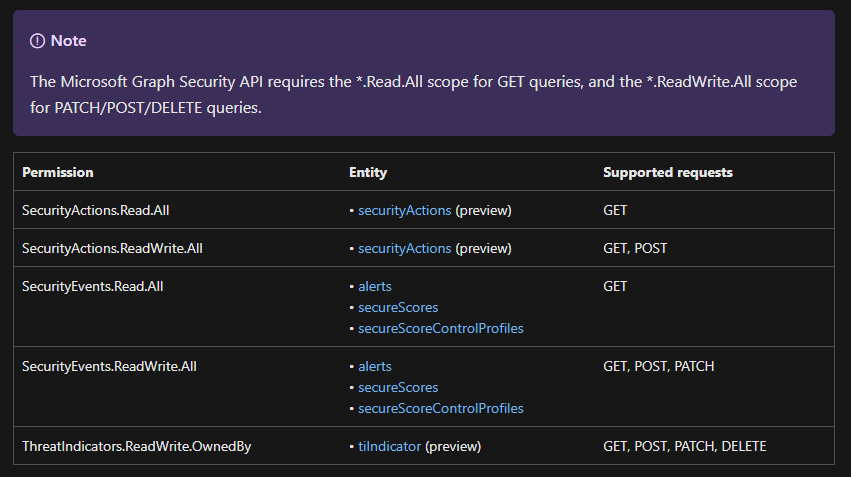
Microsoft Graph permission
As a quick refresher, there are two types of tokens: Delegated and Application permission token. Refer to this blog for more info. For delegated case, MS Graph permission is in the ‘scp’ claim and for Application type, the permission is in the ‘roles’ claim. Refer to the security entity documentation here and here for the required permission. There is also a nice summary table in the link below:
Authorization and the Microsoft Graph Security API – Microsoft Graph | Microsoft Docs
Azure AD Admin roles
For delegated permission token, the authenticating user needs to be in one of the following admin roles
| Azure AD Role | Role Template ID |
|---|---|
| Security Reader | 5d6b6bb7-de71-4623-b4af-96380a352509 |
| Security Administrator | 194ae4cb-b126-40b2-bd5b-6091b380977d |
| Global Administrator | 62e90394-69f5-4237-9190-012177145e10 |
Refer to the following documentation for more info:
Azure AD built-in roles – Azure Active Directory – Microsoft Entra | Microsoft Docs
Authorization and the Microsoft Graph Security API – Microsoft Graph | Microsoft Docs
The ‘wids’ claim in the token contains the Azure AD Role info, which is used to determine if the user has sufficient privilege.
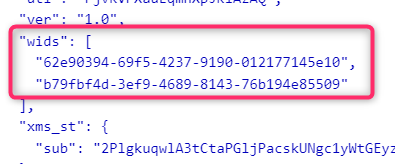
Note: the ‘wids’ claim may not exist if the token is obtained via Implicit grant flow. See Microsoft identity platform access tokens – Microsoft Entra | Microsoft Docs for more info. Use a different OAuth 2 grant flow for example Auth Code Grant flow to obtain the access token instead of.