Let’s get started…
You are getting the following similar message…
AADSTS650056: Misconfigured application. This could be due to one of the following: The client has not listed any permissions for ‘AAD Graph’ in the requested permissions in the client’s application registration. Or, The admin has not consented in the tenant. Or, Check the application identifier in the request to ensure it matches the configured client application identifier. Please contact your admin to fix the configuration or consent on behalf of the tenant.
Ensure you are accessing the application from the sign-in address provided by the application owner. Otherwise meaning, sign in to the application through its normal process. In most cases this will auto-resolve naturally. If it doesn’t, then this post can help troubleshoot and resolve it.
If your organization owns the application (meaing the application registration is in your organization)…
At minimum, we do recommended the User.Read or openid delegated permission from Microsoft Graph is added.
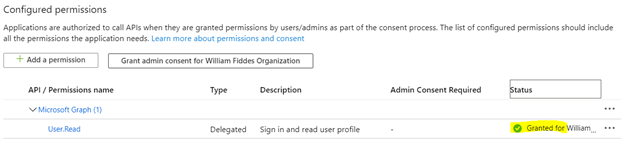
Ensure the application and all of its permissions are consented to. You can verify this by looking at the Status column of the Application registration within API Permissions. For example, this User.Read permission has not been consented to yet…
If it is successfully consented, then it will look something like this…
For application owners developing a Multi-tenant application, you will make your customers lives much easier when consenting to your application when you can add the User.Read delegated permission in addition to your other permission requirements.
In some scenarios, the application might be third-party however it may be registered in your organization. Confirm if this application is listed in your App registrations (Not Enterprise applications).
If you continue to see this error message. Then you may need to build the consent URL described below.
If your organization is not the application owner and using it as a third-party application…
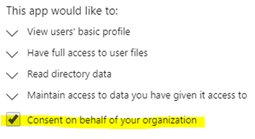
If you’re the Global/Company administrator, you should see the consent screen. Make sure you check the box for “Consent on behalf of your organization“
If you don’t see the consent screen, delete the Enterprise application, and try again.
For example…
If you continue to see this error message. Then you may need to build the consent URL described below.
Manually build the consent URL to be used.
If the application is designed to access a specific resource, you may not be able to use the Consent buttons from the Azure portal, you will need to manually generate your own consent URL and use this.
When using our authorization V1 endpoint, it will look something like this…
https://login.microsoftonline.com/{Tenant-Id}/oauth2/authorize
?response_type=code
&client_id={App-Id}
&resource={App-Uri-Id}
&scope=openid
&prompt=consent
For example…
https://login.microsoftonline.com/contoso.onmicrosoft.com/oauth2/authorize ?response_type=code &client_id=044abcc4-914c-4444-9c3f-48cc3140b6b4 &resource=https://vault.azure.net/ &scope=openid &prompt=consent
When using our authorization V2 endpoint, it will look something like this…
https://login.microsoftonline.com/{Tenant-Id}/oauth2/v2.0/authorize
?response_type=code
&client_id={App-Id}
&scope=openid+{App-Uri-Id}/{Scope-Name}
&prompt=consent
For example…
https://login.microsoftonline.com/contoso.onmicrosoft.com/oauth2/v2.0/authorize ?response_type=code &client_id=044abcc4-914c-4444-9c3f-48cc3140b6b4 &scope=openid+https://vault.azure.net/user_impersonation &prompt=consent
If the application is accessing itself for the resource, then the {App-Id} and {App-Uri-Id} will be the same.
You will need to get the {App-Id} and the {App-Uri-Id} from the application owner. {Tenant-Id} will be your tenant identifier. This will either be yourdomain.onmicrosoft.com or your directory ID…