Microsoft Graph API can be used to get different types of Sign-In event similar to what’s available in the Azure AD portal
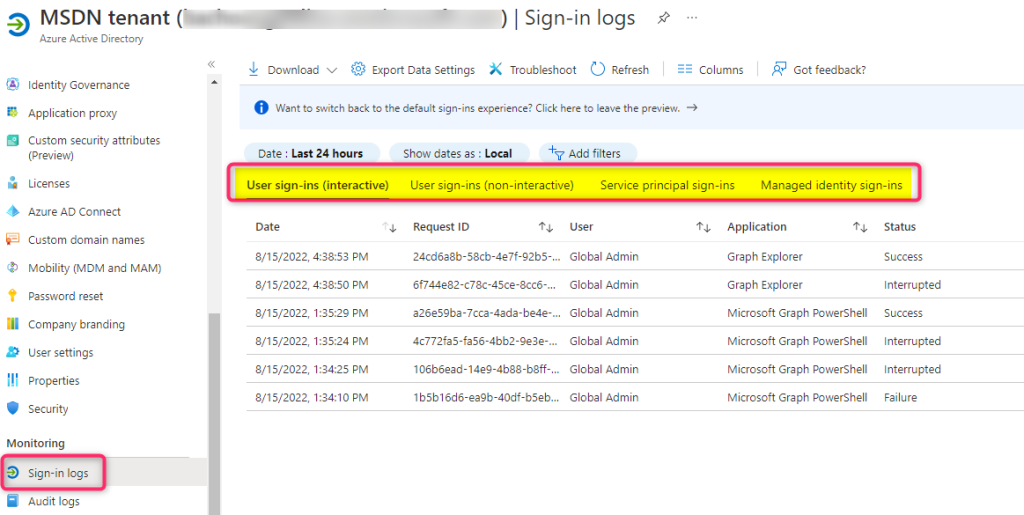
As of this writing, this functionality is only available in the beta endpoint. By default the following MS Graph request only gets a list of interactive user sign-ins
GET https://graph.microsoft.com/beta/auditLogs/signIns
To pull the other types of Sign-In logw you will have to use signInEventTypes filter query as followed:
# Get non Interactive user Sign-Ins GET https://graph.microsoft.com/beta/auditLogs/signins?&$filter=(signInEventTypes/any(t: t eq 'nonInteractiveUser')) # Get Application/Service Principals sign-ins (client credentials grant flow) GET https://graph.microsoft.com/beta/auditLogs/signins?&$filter=(signInEventTypes/any(t: t eq 'servicePrincipal')) # Get Managed Identities Sign-Ins GET https://graph.microsoft.com/beta/auditLogs/signins?&$filter=(signInEventTypes/any(t: t eq 'managedIdentity'))
Required Permission
The following permissions are required to call this endpoint:
MS Graph permissions: AuditLog.Read.All and Directory.Read.All
Azure AD Role: the authenticating principal needs to be in one of these admin roles: Security Reader, Security Operator, Security Administrator, Reports Reader, Global Reader, and Global Administrator.
MS Graph PowerShell
One can also use the MS Graph PowerShell SDK to pull the same sign in logs. Below is an example code snippet getting a list of non interactive user sign-ins
Select-MgProfile -Name "beta" Connect-MgGraph -Scopes "AuditLog.Read.All","Directory.Read.All" Write-Host "Getting NonInteractive User Sign ins" Get-MgAuditLogSignIn -Filter "(signInEventTypes/any(t: t eq 'noninteractiveUser'))" -Sort "createdDateTime DESC" DisConnect-MgGraph