Problem:
You may see the error “Authorizaion_RequestDenied” below
'error': {
'code': 'Authorization_RequestDenied',
'message': 'Insufficient privileges to complete the operation.',
'innerError': {
'date': '2020-11-09T20:28:42',
'request-id': '604e410b-4af8-4b79-9f48-fe0cf905a759',
'client-request-id': 'd6350bb5-3660-1f44-01a8-8a3b86a4c12a'
}
}
when using Microsoft Graph to manage users. The error happens most likely because the user does not have sufficient permissions. In summary the call requires both of the following:
1) The user or application needs to be in an Administrative role
2) The MS Graph access needs to have the proper permissions.
In this blog post, I will demonstrate a couple of things using postman for Delegated and Application permissions
- How to enable or disable the user.
- How to create or delete the users.
Requirement: You must have a client Application registered in Azure Active Directory and configure the proper permissions (Delegated and/or Application) which I will discuss below.To understand the difference between Delegated and Application permission refer to difference between application permission and delegated permission | Azure Active Directory Developer Support Team (aaddevsup.xyz).
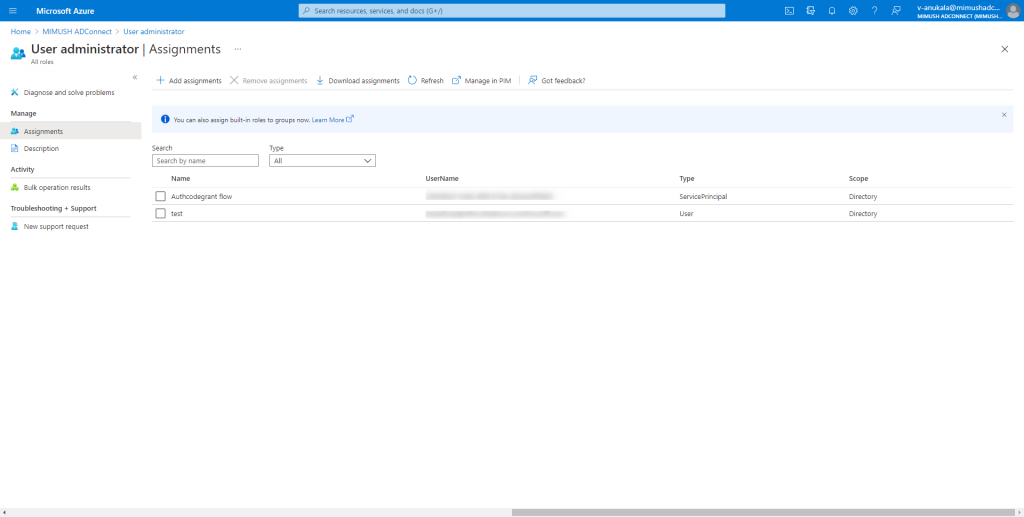
The authenticating principal (user or application) that logs in to Azure AD and get an Access Token needs to be in the following Azure AD Admin Roles: User Administrator or Global Admin. Below is my sample screenshot to check the specific roles of my user.
For Azure AD built-in Administrative roles refer to the link below.
Azure AD built-in roles – Azure Active Directory | Microsoft Docs
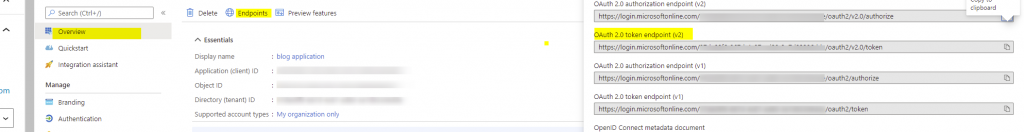
Below is my sample app registration. In the overview blade, take note of the Application (client) ID, Directory (tenant) ID fields, token and the authorize endpoints as you will need to configure those in Postman.
To enable or disable user accounts we need to send a PATCH request to the user end point
PATCH https://graph.microsoft.com/v1.0/users/<UPN or Object ID> request body:
{
“accountEnabled”: true or false
}
The required Microsoft Graph permission is listed in the link below.
Update user – Microsoft Graph v1.0 | Microsoft Docs
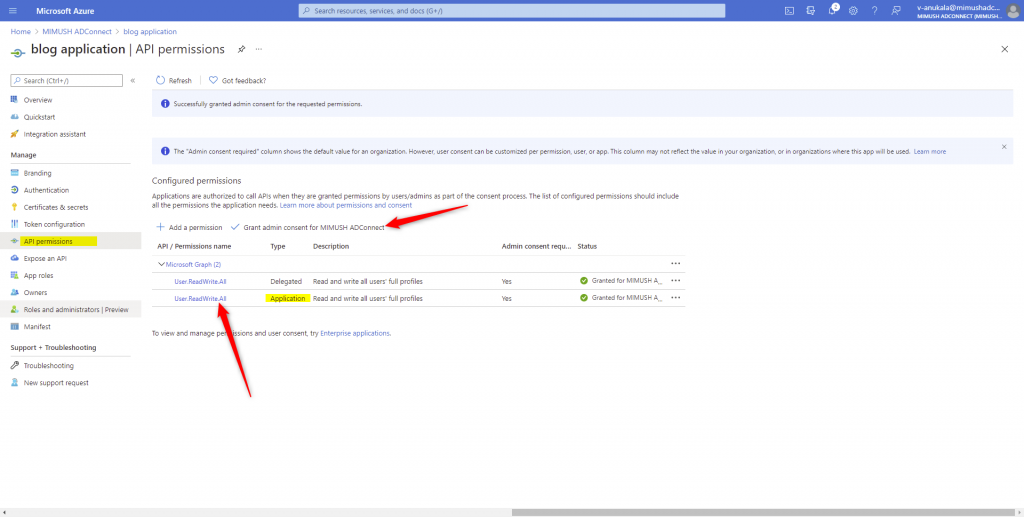
For my sample app, I use User.ReadWrite.All permission
Note: You need to Grant Admin Consent to these permissions before requesting an access token.
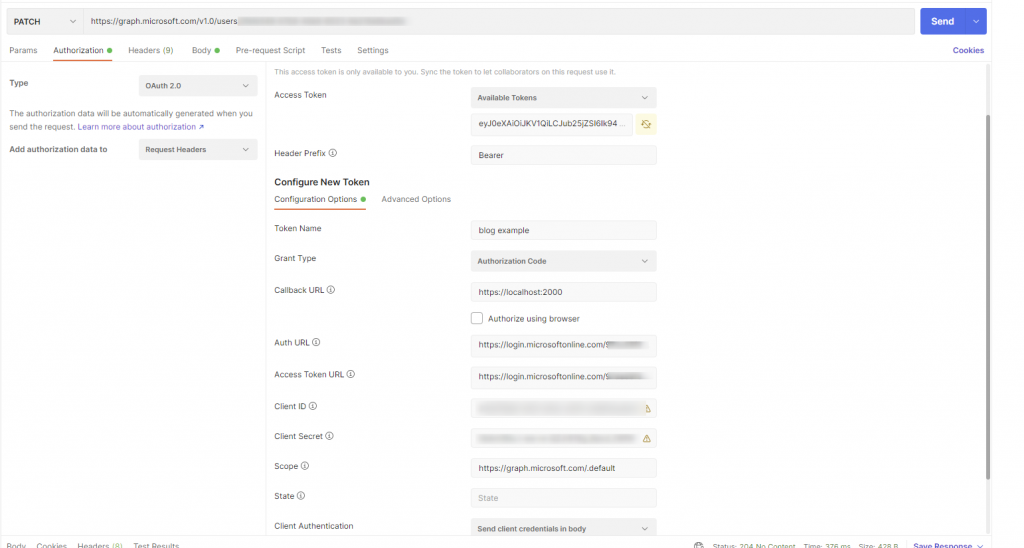
using Postman to configure the access token and Make the call to the user endpoint using
1) Delated permissions.
Note: For delegated permission token, the permission shows up in the scp claim (decoded using https://jwt.ms)
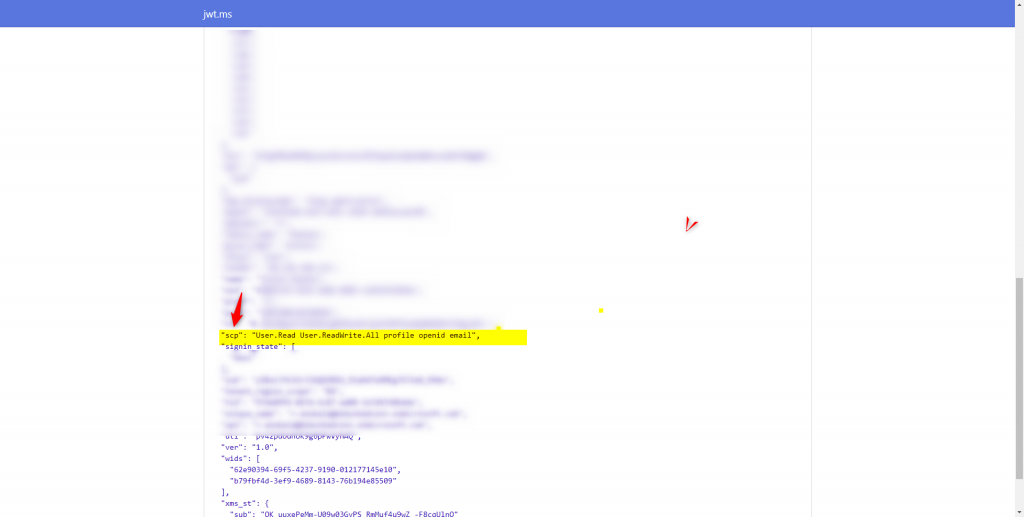
2) For application permission
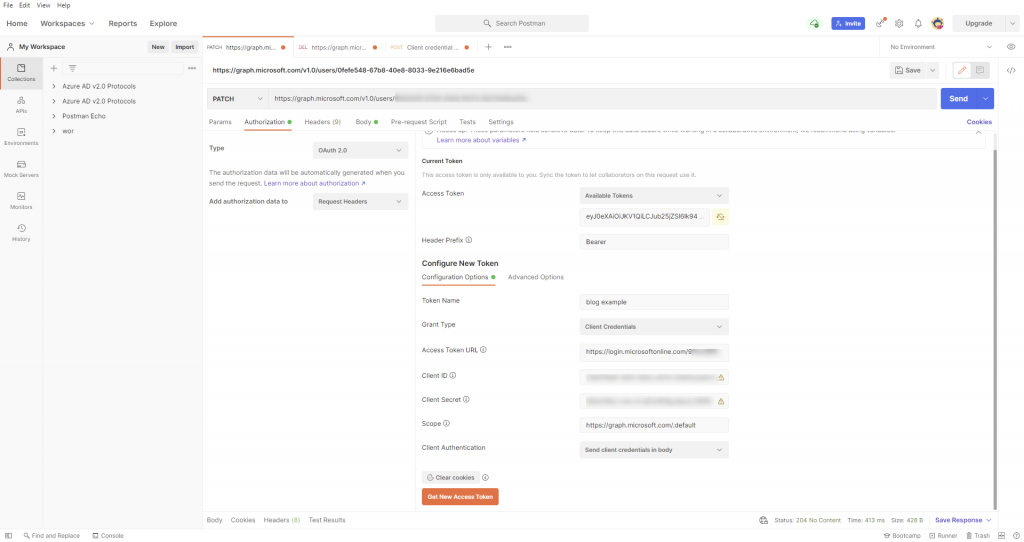
Note: For application permission token, the permission shows up in the roles claim (decoded using https://jwt.ms)
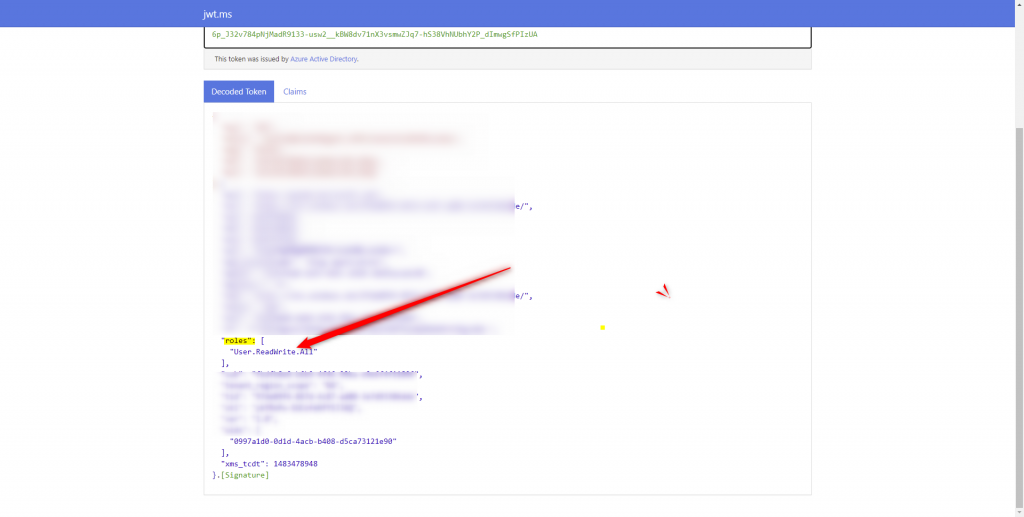
For creating and deleting users, refer to the MS Graph documentation below for required MS Graph permission (make sure the permissions are admin consented before getting a token). The process for getting access tokens is the same as above
Create User – Microsoft Graph v1.0 | Microsoft Docs
Delete a user – Microsoft Graph API – Microsoft Graph v1.0 | Microsoft Docs
1) Create an user using Delegated/Application Permissions.
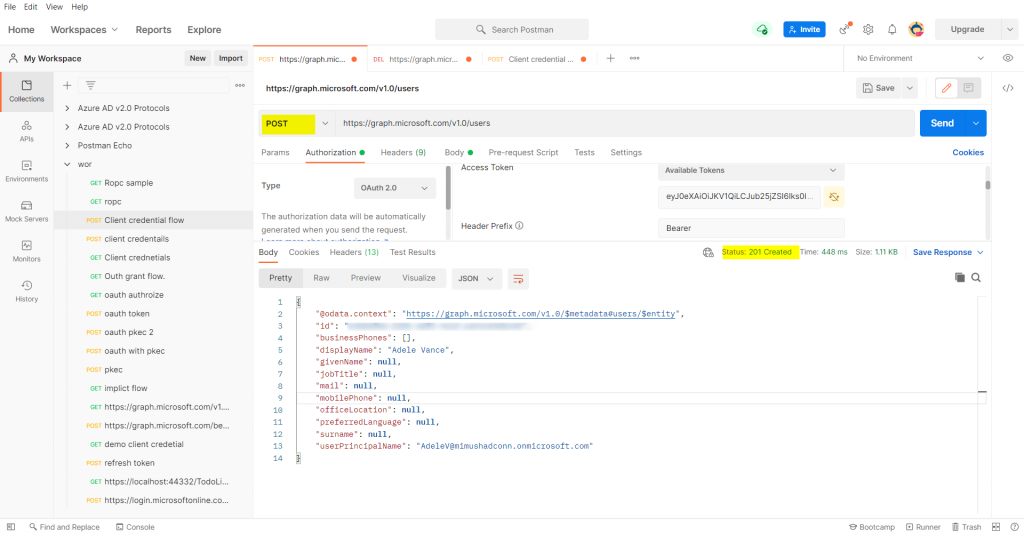
2)Delete a user using Delegated/Application Permissions.
For permissions, add the least privileged delegated permission Directory.AccessAsUser.All.The application permission would be User.ReadWrite.All.
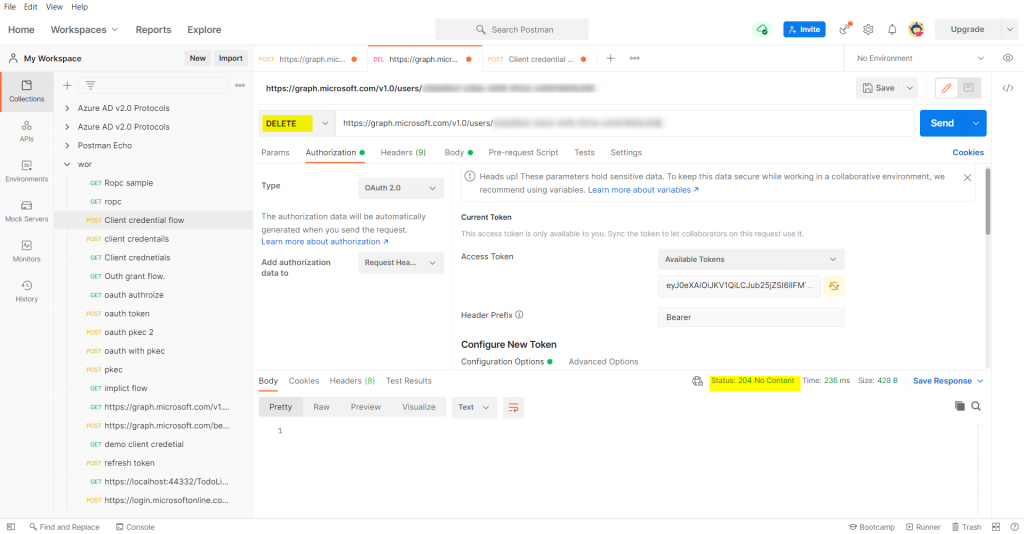
Using postman to delete the user I created previously using the delegated,application permissions.
I followed the steps and still got the same error. I can successfully create users, but I cannot reset password nor update user info.
I tried using the latest version of Microsoft.Graph 5.31.0 and I get exception Microsoft.Graph.Models.ODataErrors.ODataError
Message The expression cannot be evaluated. A common cause of this error is attempting to pass a lambda into a delegate. string
Then I downgraded to 4.54.0 and I can successfully create new users, but when updating then password, I get error:
Code: Authorization_RequestDenied
Message: Insufficient privileges to complete the operation
I am using AD B2C.
It may be worth to open a support case for this. Azure AD B2C locks down a lot of MS Graph permission so you will not be able to use delegated permisison token to manage users. You will probably need to use Application permission for that. You can look at https://learn.microsoft.com/en-us/azure/active-directory-b2c/microsoft-graph-operations#how-to-programmatically-manage-microsoft-graph for more information.