To use the V1 endpoint, please refer to this post. Our documentation for the client credentials grant type can be found here.
You can setup postman to make a client_credentials grant flow to obtain an access token and make a graph call ( or any other call that supports application permissions ). This is very useful for testing code you plan to run as a script or in a Daemon application where you do not want user interaction.
The first thing you need is an app registration in your Azure Tenant to perform this flow. Create a new application registration:
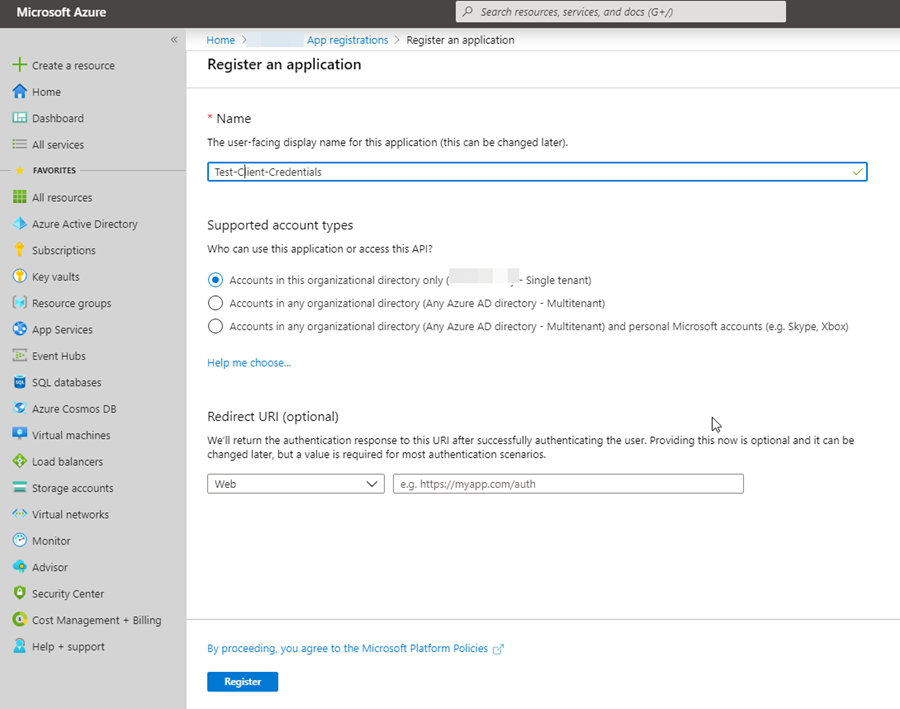
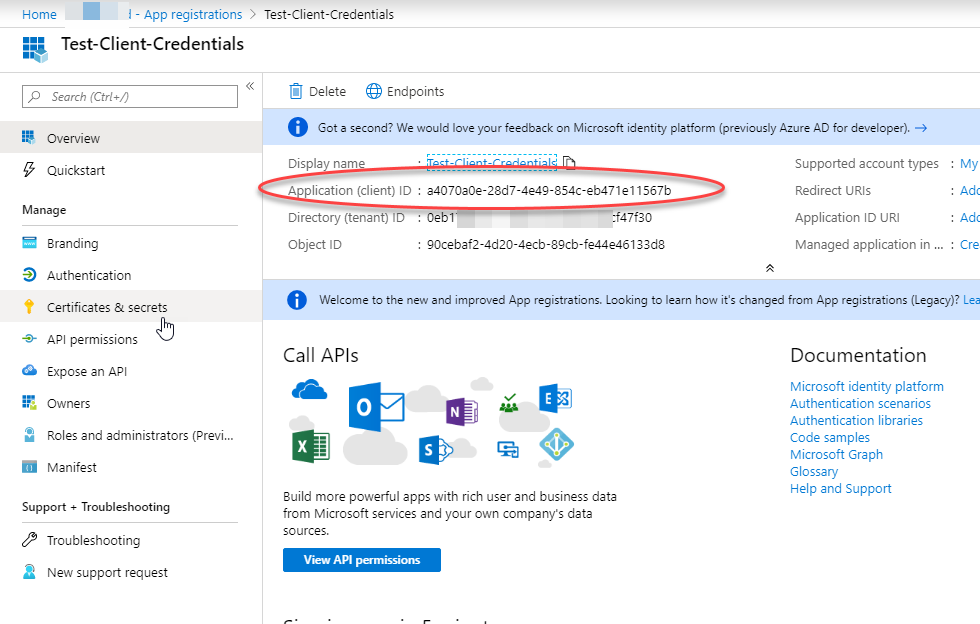
Note the application id as you will need it later – this is the client_id used in the setup for postman:
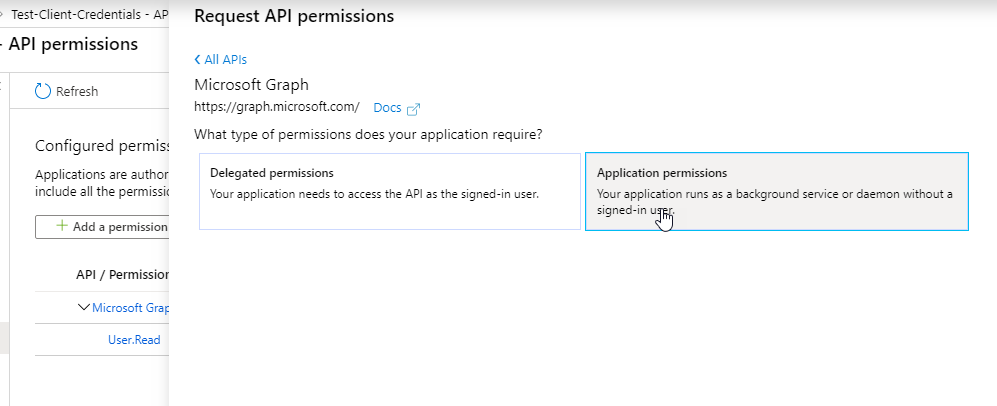
Click on the API permissions and assign application permissions. By default, Microsoft Graph is already selected with a delegated permission of User.Read. I will leave that there to demonstrate that permission will not be present in the access token when performing this flow. Lets add an application permission for Microsoft Graph of Group.Read.All :
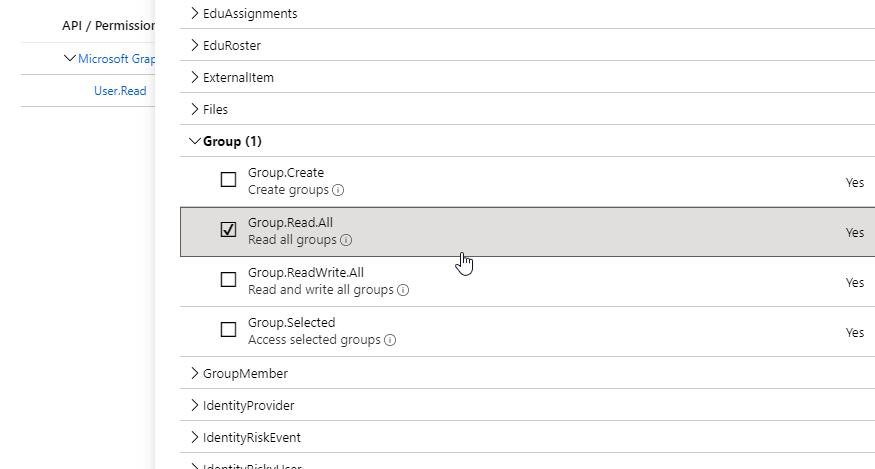
Once added, you will now see your permission listed however, all application permissions always require a tenant admin to consent to these permissions:
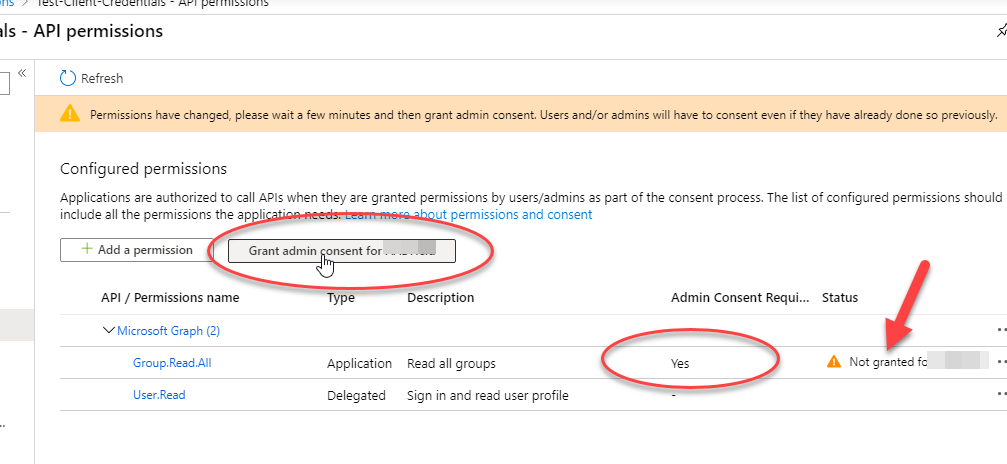
Grant admin consent:
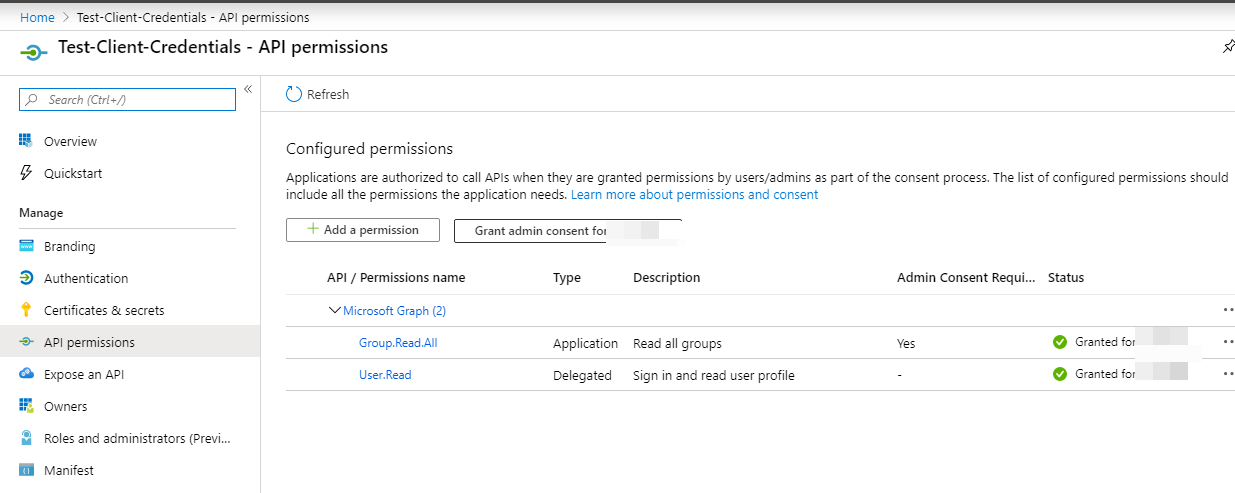
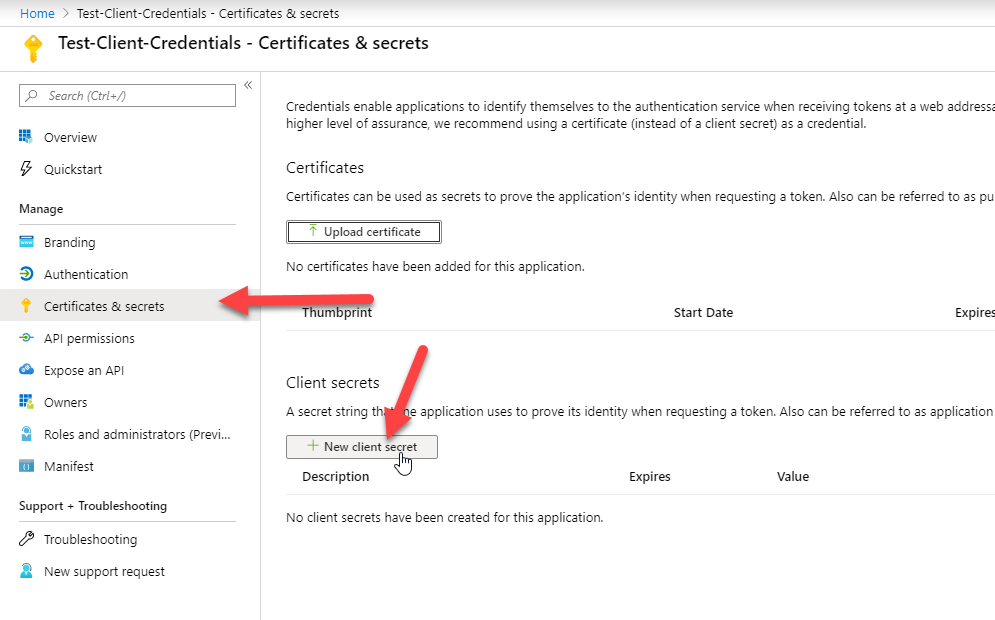
Next, the client_credentials flow requires a client secret. Go to the Certificates and Secrets blade and create a new client secret:
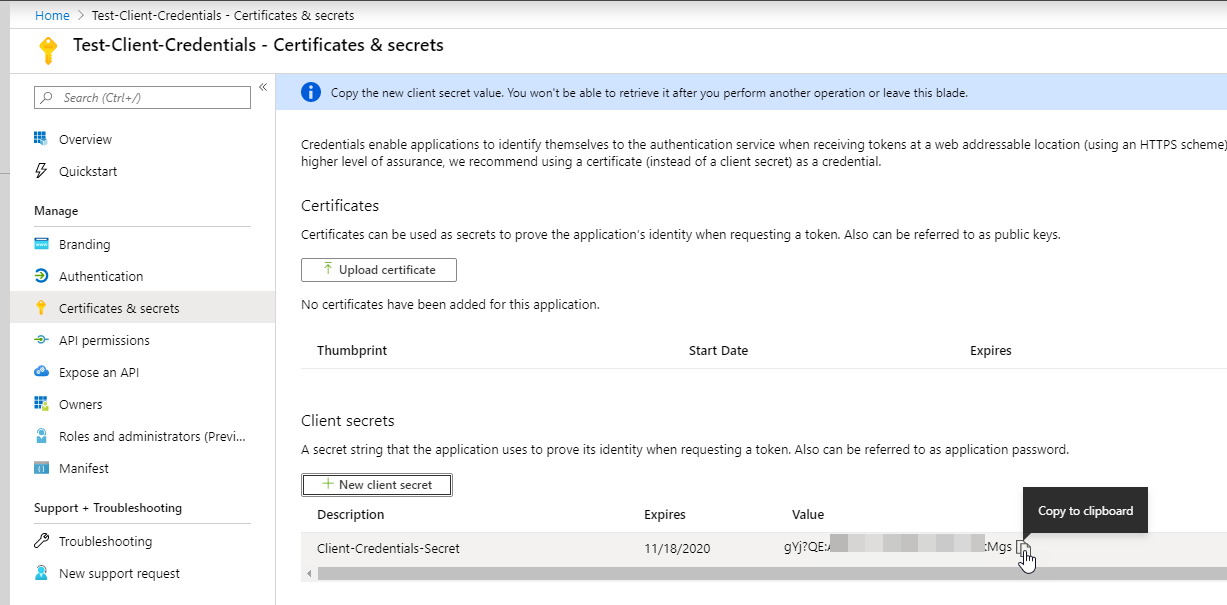
The value is only shown one time so be sure to copy it to the clipboard with the copy to clipboard button and store that somewhere safe. You don’t want that secret to get out!
The first method I will demonstrate to you for obtaining an access token with Postman is through the Authorization UI. Start a new request, then click on the Authorization tab and select OAuth 2.0 from the drop-down type list:
To configure the flow, select Client Credentials from the Grant Type drop-down box then plug in your values for the settings it requests. For the scope, I am using https://graph.microsoft.com/.default which will pull the default values configured for Microsoft Graph from the app registration – in this case, we are expecting the groups.read.all permission. Use https://login.microsoftonline.com/{your-tenant}/oauth2/v2.0/token/ for the Access token URL ( obtained from the portal “Endpoints” – see next image ), the client id from the app registration and of course, the client_secret you configured on the app registration.
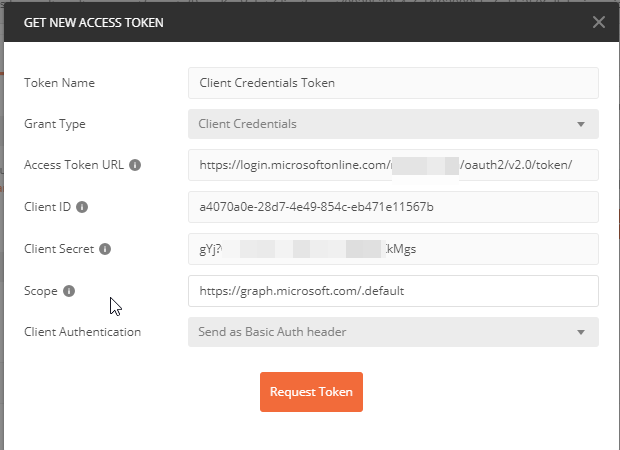
The Access Token URL can be obtained from the portal in the App Registrations blade by clicking on the “Endpoints” button:
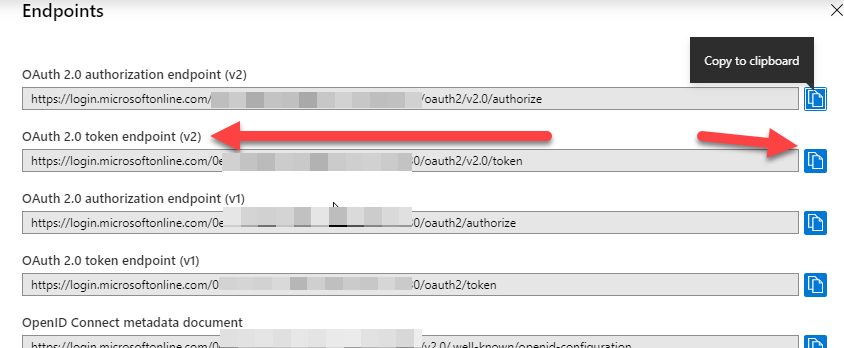
Grab the OAuth 2.0 token endpoint (v2). You can also use your tenant name in place of the tenant id ( guid ):
Save those values in the postman screen and then click on “Request Token”
You should get an access token like so:
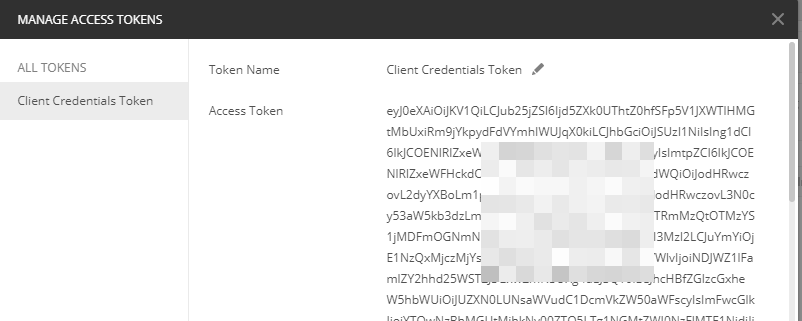
To use this token, scroll to the bottom and click on the “Use Token” button:
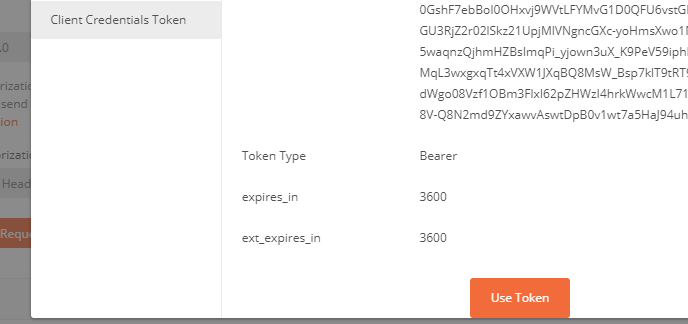
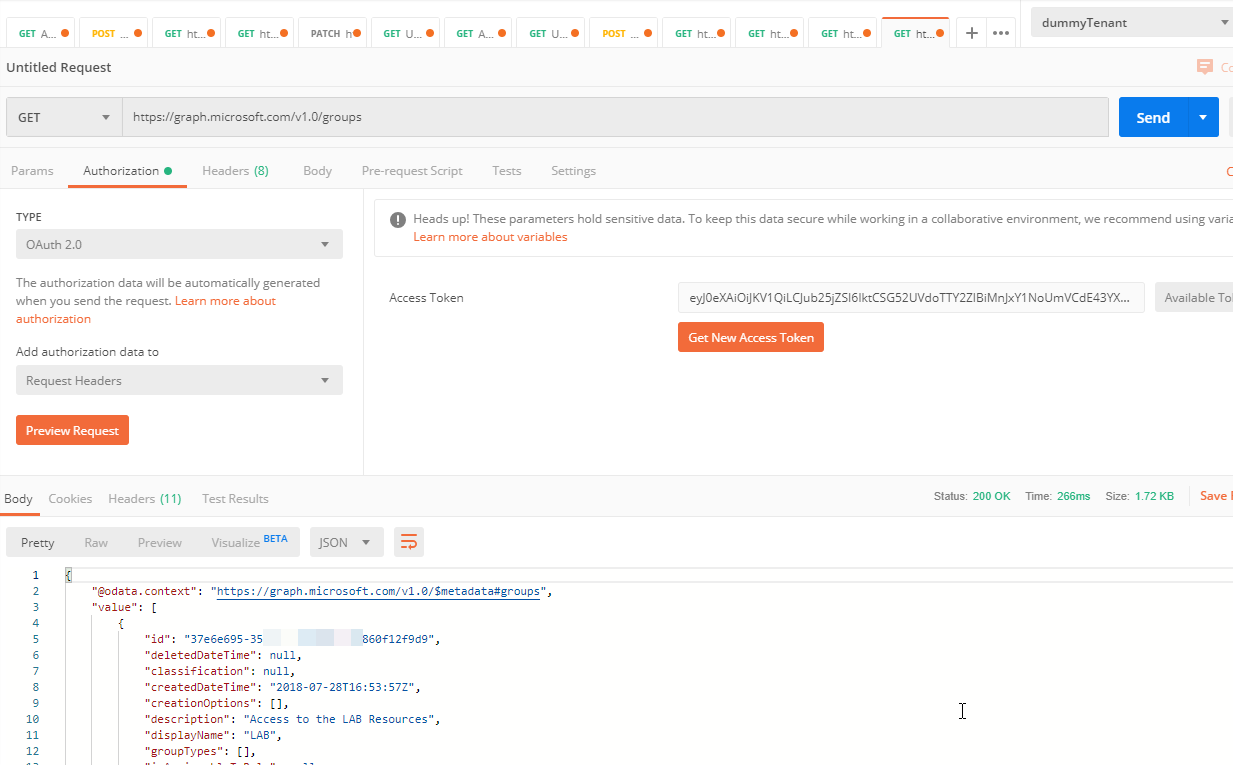
You can now make a graph call ( based on the permissions you setup in the app registration – groups in this example ) – the rest endpoint in this example is https://graph.microsoft.com/v1.0/groups :
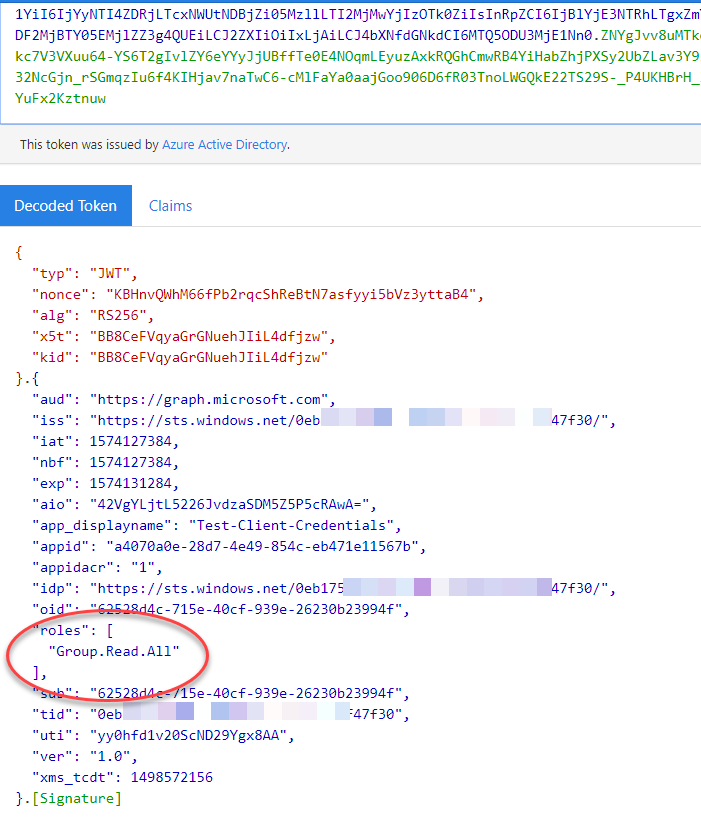
If you copy the access token and paste it in http://jwt.ms you can decode the token to see the claims it has. If you notice, our token only has permissions for group.read.all – which shows up as a “role”. Application permissions always show up as roles. Notice, there is not a delegated permission in this token because delegated permissions, even if consented to, will not appear in the token for a client_credentials grant type.
You can also just do a raw post request to the authority endpoint with the same values like this, again, you need to add the client_id, client_secret, scope but you also need to add grant_type when doing it this way and for that value, be sure to use “client_credentials”:
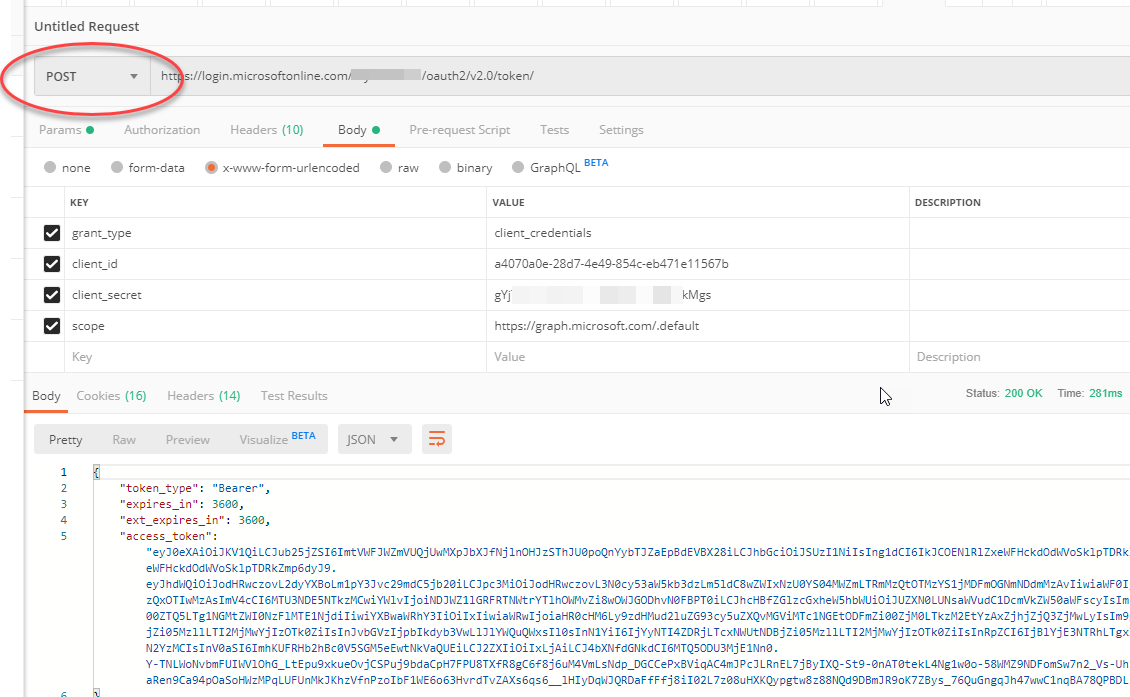
The values go in the body of the request in this scenario.
Summary:
You can use postman to obtain an access token for testing your api calls, etc. using the client_credentials flow as demonstrated.