Introduction
As documented here, the Microsoft Graph Reporting API can be used to get the audit logs (https://graph.microsoft.com/beta/auditLogs/directoryAudits) and the sign-ins reports (https://graph.microsoft.com/beta/auditLogs/signIns). The old reports endpoint using Azure AD Graph is now deprecated
and attempting to use that legacy end point to get the auditEvents can result in the following error:
GET https://graph.windows.net/<tenant>.onmicrosoft.com/reports/auditEvents?api-version=beta
{
“error”:{
“code”:”Deprecated_ActivityReports”,”message”:”This API is deprecated as part of old azure classic portal, please use the API https://graph.windows.net/$tenantdomain/activities/. For more information refer the documentation https://docs.microsoft.com/en-us/azure/active-directory/active-directory-reporting-api-getting-started-azure-portal.. CorrelationID:10242ee6-2aa7-4173-826a-dc0fe898a87b timestamp:2019-04-12 13:00:05Z”
}
}
Using the new end point…
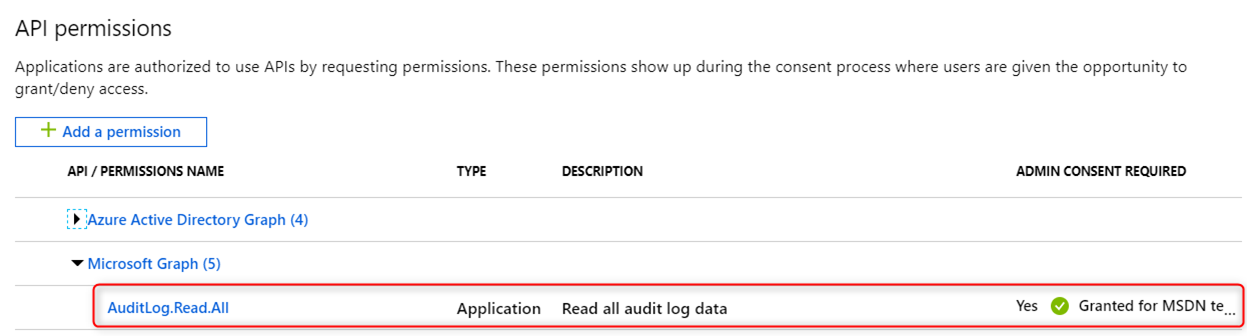
Make sure you refer to the Reporting API prerequisite page for pre-requisites on accessing the Azure AD reporting API. For Application Permission token, make sure the application has AuditLog.Read.All Application permission and that permission is given admin consent.
Note that the reporting API guidance at https://github.com/toddkitta/azure-content/blob/master/articles/active-directory/active-directory-reporting-api-getting-started.md is outdated. In this blog post, I’ll show how to modify the PowerShell script to use the new MS Reporting API to get the Audit logs for the last 2 days. The new endpoint we want to use is https://graph.microsoft.com/beta/auditLogs/directoryAudits. See documentation for more info on directoryAudits. Below is the entire PS script using reporting API.
Note: You still need to follow the set up instruction at https://github.com/toddkitta/azure-content/blob/master/articles/active-directory/active-directory-reporting-api-getting-started.md to create an application registration and make sure to configure Microsoft Graph for API permission. Replace the ClientID, ClientSecret, and tenantdomain with your information.
[gist id=”0ce05bbc3ff4fcb51b3a61e0353c404e” file=GetReportingApi.ps1″”]
The above script can be easily modified to get the sign-ins report. An Azure AD Premium P1 license is required to get the sign-ins data. Please review Azure AD audit log API overview and Reporting API tutorial prerequisite for more detail.
Thanks for reading and drop us a comment if this content helps.