By default, when you sign out of Azure Active Directory when using a Open ID Connect/OAuth2 application, you will be prompted to select a user account to sign out of, even if there is only one user account to select.
To work around this behavior, there are 3 requirements:
Step (1): Add the optional claim for the login_hint
Add the login_hint optional claim to the id token in the App Registration blade
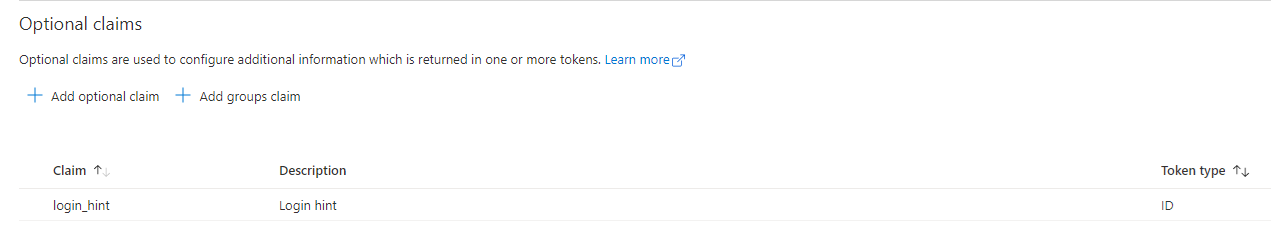
For more information about adding optional claims:
https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-optional-claims
Step (2): Ensure “profile” and “openid” openid connect scopes are in the original sign-in request
If your using the Authorization code flow…
When the sign-in request is sent, make sure both “openid” and “profile” is listed in the scope. For example:
https://login.microsoftonline.com/contoso.onmicrosoft.com/oauth2/v2.0/authorize?response_type=code&client_id=83258bc7-b7fd-4627-ae9b-e3bd5d550572&scope=openid+user.read+profile&redirect_uri=https://login.microsoftonline.com/common/oauth2/nativeclient
During the token endpoint call, when you acquire a access token, an id_token is also returned.
If your using the implicit flow (not recommended)…
https://login.microsoftonline.com/contoso.onmicrosoft.com/oauth2/v2.0/authorize?response_type=id_token&client_id=83258bc7-b7fd-4627-ae9b-e3bd5d550572&scope=openid+user.read+profile&redirect_uri=https://login.microsoftonline.com/common/oauth2/nativeclient
After sign-in, when Azure AD redirects back to your application, the id_token will be returned.
On the returned id_token…
The login_hint claim will be returned in the id_token and will look similar to:
O.CiQ0M2E1NDg4Yy05ZGU2LTQyZTUtYWJkZS0zY2IzNGU4ZjBlZGMSJGFhMDBkMWZhLTUyNjktNGUxYy1iMDZkLTMwODY4Mzc…
Step (3): Logout request
When sending the logout request, pass a logout_hint parameter where login_hint is the value:
https://login.microsoftonline.com/williamfiddes.onmicrosoft.com/oauth2/v2.0/logout?post_logout_redirect_uri=https://login.microsoftonline.com/common/oauth2/nativeclient&logout_hint=O.CiQ0M2E1NDg4Yy05ZGU2LTQyZTUtYWJkZS0zY2IzNGU4ZjBlZGMSJGFhMDBkMWZhLTUyNjktNGUxYy1iMDZkLTMwODY4Mzc…
More Information
When using MSAL.js, the code will look like this (MSAL.js will auto send the logout_hint if detected when you send a EndSessionRequest with the account)
logout() {
var account = this.authService.instance.getAllAccounts()[0];
let logoutRequest:EndSessionRequest = {
account: account
};
this.authService.logout(logoutRequest);
}
When using Microsoft Identity Web or AspNet (Core) OpenIdConnect Authentication
services.Configure<OpenIdConnectOptions>(OpenIdConnectDefaults.AuthenticationScheme, options =>
{
// Custom code here.
options.Events.OnRedirectToIdentityProviderForSignOut = (context) =>
{
var login_hint = context.HttpContext.User.Claims.Where(c => c.Type == "login_hint").FirstOrDefault();
if (login_hint != null)
{
context.ProtocolMessage.SetParameter("logout_hint", login_hint.Value);
};
return Task.FromResult(true);
};
});