We get this kind of question all the time. It comes in many variations and forms like…
“I only want to consent for some users to access the app.”
“I only want my service account to access this app”
Before we get started…
First and foremost, only consenting for allowed users is not the solution. This is not the purpose for consent. Consent is to inform a user or admin what the application is accessing and to give the user or admin an option to accept or deny the requested permissions. Administrators should not be using this to determine who has access to an application. Once the permissions are consented, then we will only allow the app to access the requested permissions and no more.
For more information about the Azure AD Consent Framework…
https://docs.microsoft.com/en-us/azure/active-directory/develop/consent-framework
Let’s get started…
If you want to control access to an application, then you should be enabling the requirement of user assignment on the Enterprise application then assign the user, group, or service principal to the application.
First: Perform admin consent
Make sure an administrator has performed an Admin consent on the required permissions. This is a requirement in order to restrict user access. Otherwise, you will see various consent related messages or you need admin approval.
For troubleshooting consent issues, see the following article…
Second: Enable User assignment required…
Third: Assign users, groups, service principals
Once user assignment is required, now assign the user, groups, or service principal to the application…
If it’s a Web Application…
If it’s a Public Client…
If the application is enabled as a Public Client type so that you can use Windows Authentication, Resource Owner Password Credential flow, or Device Code flow, then this is a bit trickier…
- First, disable the Public Client configuration within the application registration…
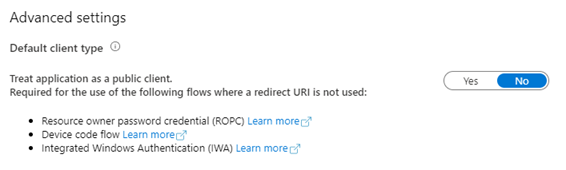
- Then perform the step above under “If it’s a Web Application” to assign users, groups, or service principals to the application.
- Then re-enable the Public Client configuration.
Optionally, you can also use Azure AD PowerShell… (Especially if you do not own the application to disable Public client type.)
When user assignment is required…
Once user assignment is required, then only those users will be able to access the application. Users who do not have access will get the following similar error message…
AADSTS50105: The signed in user ‘{EmailHidden}’ is not assigned to a role for the application ‘{app-id}'({app-display-name}).
Other Tips…
You can also do this for other resources such as an API. Just follow the steps above applying them to the resource’s Enterprise app. Be careful and don’t do this for Microsoft first-party apps as you might break apps like Outlook, Power BI, SharePoint, ect…