Last Updated: August 23 2019
Let’s get started…
When your developing or integrating an application with Azure AD, you might see the following similar error…
AADSTS50011: The reply url specified in the request does not match the reply urls configured for the application: ‘XXX’.
This is because the redirect_uri (when using OpenID Connect) or AssertionConsumerServiceUrl (when using SAML2) being passed to Azure Active Directory to sign-in, does not exist in the application registration.
For example, if using OpenID Connect, your authentication request might look something like this…
https://login.microsoftonline.com/common/oauth2/authorize?response_type=code
&client_id=99f00653-5600-45d1-aa19-57a297ad0a58&redirect_uri=https://www.contoso.com/signin-oidc
If you are signing in using a browser, you can also see this sign-in request in the browsers address bar on the error screen.
So, we are going to check if https://www.contoso.com/signin-oidc is a reply address in the application registration for 99f00653-5600-45d1-aa19-57a297ad0a58…
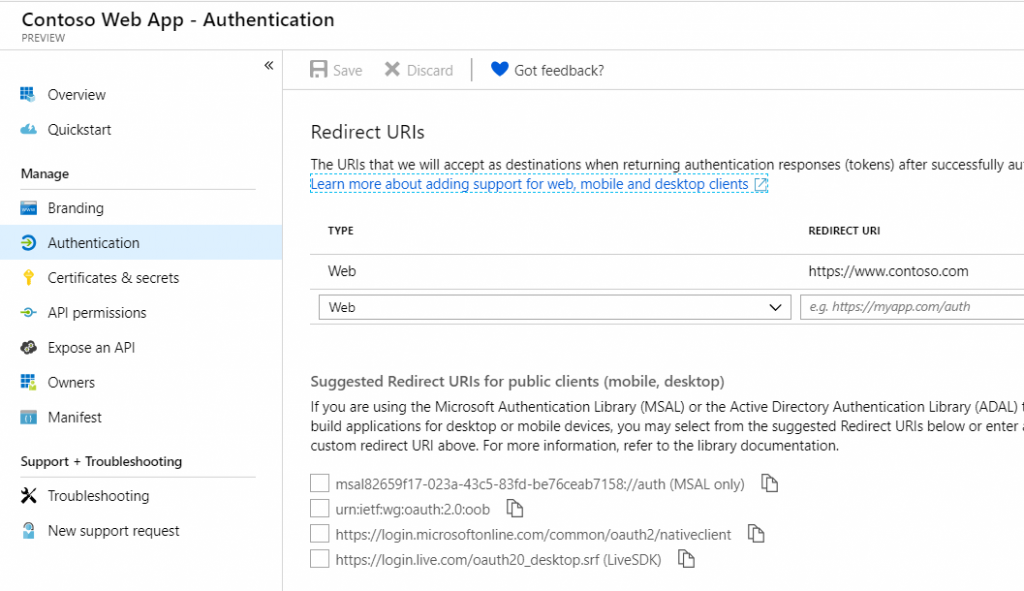
We got the error because https://www.contoso.com/signin-oidc is not added as a reply address in the application registration.
For SAML authentication, The sign-in request might look something like this…
https://login.microsoftonline.com/common/saml2?SAMLRequest=jZHNS8NAEMXvgv9D2Hu...
The SAMLRequest is going to look like a long value of random characters. We call this a Base64 encoded string that is SAML enflated. So to ‘deflate’ this in order to read the contents of the SAMLRequest, you can use the TextWizard in Fiddler or use a tool like the one below…
https://www.samltool.com/decode.php
Once the SAMLRequest is deflated, it will look something like this…
<samlp:AuthnRequest
xmlns="urn:oasis:names:tc:SAML:2.0:metadata"
ID="id6c1c178c166d486687be4aaf5e482730"
Version="2.0" IssueInstant="2013-03-18T03:28:54.1839884Z"
xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
AssertionConsumerServiceURL="https://www.contoso.com">
<Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion">https://www.contoso.com</Issuer>
<NameIDPolicy Format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent"/>
</samlp:AuthnRequest>
The Assertion Consumer Service (ACS) within the SAMLRequest resembles the reply address.
So, we are going to check if ‘https://www.contoso.com‘ is a reply address in the application registration for the application ‘https://www.contoso.com’ which is identified by the apps ‘Identifier (Entity ID)’ in Azure Active Directory.
So what’s the solution?
So, to resolve this, you guessed it, ensure the redirect URI or Assertion Consumer Service URL is added to the application registration.
To do this…
- Sign into the Azure portal @ https://portal.azure.com
- Go to Azure Active Directory.
- Go to Application registrations.
- Find your app.
- Go to Authentication under Manage.
- Review your registered Redirect Uri(s).
How to determine what reply address is being used…
If you’re not sure how to collect this information, we generally like to use a HTTPS capturing tool like Fiddler (Available for Windows, macOS, and Linux).
To learn more about how you can use Fiddler, see the following article…
https://blogs.aaddevsup.xyz/2018/09/12/capture-https-traffic-with-http-fiddler/
You can look at the details of your request to Azure AD. Use the following article as a guide…
https://docs.telerik.com/fiddler/Observe-Traffic/Tasks/ViewSessionContent