Introduction
This article is broken up into a couple of different sections based on what you are trying to do.
Trying to modify the service principals credentials typically is meant for accessing an application that is multi-tenanted and the client secret has expired and they need a fix to resolve a wide outage due to an expired client secret.
This typically has to do with a key expiring, many people wish to extend their keys for their service principal however you cannot do this. You have to add a new key to your service principal moving forward.
By changing the enterprise application key and then rolling it out with the correct key, this will resolve the issue for all users using the application in a separate tenant.
Note that enterprise applications and service principals are the same in the Azure portal. We refer to the Service Principals as SPs or Service principals when accessing them in PowerShell. But when in the portal, they are called enterprise applications. More on enterprise applications can be found in the link : https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-application-objects Please refer to this link to learn more about the AAD Application Objects and Service Principals and how they work together.
Adding a New Secret to An Enterprise Application Using MSOL
This section is assuming that you have MSOL installed on your machine for PowerShell.
For more information about install MSOL please go here : https://docs.microsoft.com/en-us/powershell/azure/active-directory/install-msonlinev1?view=azureadps-1.0
The below PowerShell script needs the end date to be changed to whatever date you choose.
Please replace the client ID field with the client ID of your AAD Application Registration. You can find the client ID in your enterprise Application blade.
Also remember to change the $Enddate to whatever you would like the expiration date to be for your new secret.
$startdate = Get-Date $Enddate = "November 28 2029" $clientid = "xxx" # (Enter you client ID / Application ID) $ClientID = $clientid $bytes = New-Object Byte[] 32 $rand = [System.Security.Cryptography.RandomNumberGenerator]::Create() $rand.GetBytes($bytes) $rand.Dispose() $newClientSecret = [System.Convert]::ToBase64String($bytes) # (This command will provide you with the new secret. Please record it because you will not be able to get it again) $newClientSecret # (Enter an Tenant Admin account that can create Service Principal and Directory Objects) $msolcred = Get-Credential Install-Module MSOnline Connect-MsolService -credential $msolcred $AppSP = Get-MsolServicePrincipal -AppPrincipalId $ClientID # (Verify that this is the correct Application) $AppSP New-MsolServicePrincipalCredential -AppPrincipalId $AppSP.AppPrincipalId -Type password -Value $newClientSecret -StartDate $startdate -EndDate $Enddate Get-MsolServicePrincipalCredential -ObjectId $AppSP.objectId -ReturnKeyValues $true
Reading the PowerShell script we are doing these actions procedurally : get today’s date, create a random secret, and then add the secret to your service principal based on the Application ID.
Please remember to login to the correct tenant otherwise it won’t be able to find the ApplicationID.
Adding a Credential to An Enterprise Application Using Azure Resource Manager
This section will assume that you have installed the Azure Resource Manager.
Please see the following links to learn more about Azure’s PowerShell Module, this also tells you how to install AzureAD into your PowerShell environment :
https://docs.microsoft.com/en-us/powershell/azure/active-directory/install-adv2?view=azureadps-2.0
Following this guide, we will be installing the module AzureRM. Then we will be able to utilize Connect-AzureAD, I have multiple tenant IDs so I’m specifying the tenant ID I would like.
You can get the tenant ID by going to the portal and then clicking on the top right
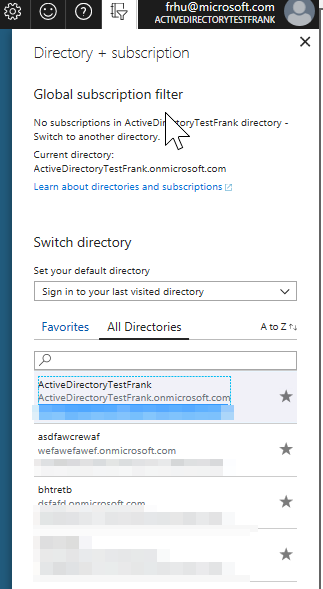
Then once we have the tenant ID we will be able to connect using connect-azuread. I have cropped out my tenant ID in the picture below.
![]()
After running this command you’ll get the interactive pop up to sign-in.

First we are going to want to get the correct service principal.
There are two ways to get the ServicePrincipal’s details.
You can get some details from the Azure Portal under enterprise applications and then clicking on the one you would like to add the secret to. From there you will want to get the Application ID.
You can get all of a service principal’s details using the command below. If you have too many enterprise applications your PowerShell might stop responding so you may have to utilize a filter to get the specific service principal you want. The documentation goes into these options to filter on a specific Service Principal. I am just listing all the service principals in the picture below.
Get-AzureADServicePrincipal, please keep track of the objectID as you will need it later. Also note that the display name and the serviceprincipalname are different.

This link goes to the documentation for getting the SPs.
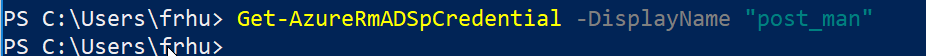
The command below will get your service principals/enterprise application credentials which are the keys
Get-AzureRMAdSPCredential, here I don’t have any credentials for the Service Principal which is why the command doesn’t return anything.
The documentation for this command is here.
The command below will create a new SP/Enterprise Application Key/credential,
New-AzureRMAdSPCredential
In the examples it shows how to utilize the commands to create a password and then to add the password to your service principal, this is also documented below. After logging in you to the correct tenant you will be able to utilize this command to add a credential to your SP.
$SecureStringPassword = ConvertTo-SecureString -String “password” -AsPlainText -Force
New-AzureRmADSpCredential -ObjectId <your-objected> -Password $SecureStringPassword
Adding Certs with Your Service Principal
The PowerShell command New-AzureRMAdSPCredential also allows you to add a certificate to your Service Principal to be used for as authentication.
This is described in the documentation linked below.
Conclusion
We have gone over how to utilize MSOL and AzureRM Powershell 2.0 to add a secret, password, and certificate to your service principal. This should help to handle users who need to add secrets passwords to your multi tenanted applications. If there are anymore issues please file a support ticket and one of our support engineer will reach out to you to resolve the issue as quickly as possible.